From the February 2022 issue of Pacific Ports Magazine
Noting the 2019 United States Coast Guard Marine Safety Information Bulletin, ports and ships are direct targets for cyberattacks. That Bulletin specifically warned commercial vessels about targeted cyberattacks where malicious actors, using email addresses that appeared to be from a Port State Control authority, sought sensitive information such as crew member’s name, personally identifiable information (PII) and protected health information (PHI), many times under the guise of COVID-19 management. Ports and ships in the maritime industry are vital points in the global supply chain for food, medicine, consumer goods, fuel and many other products. Supply chain cyberattacks jumped over 300 percent in 2021.
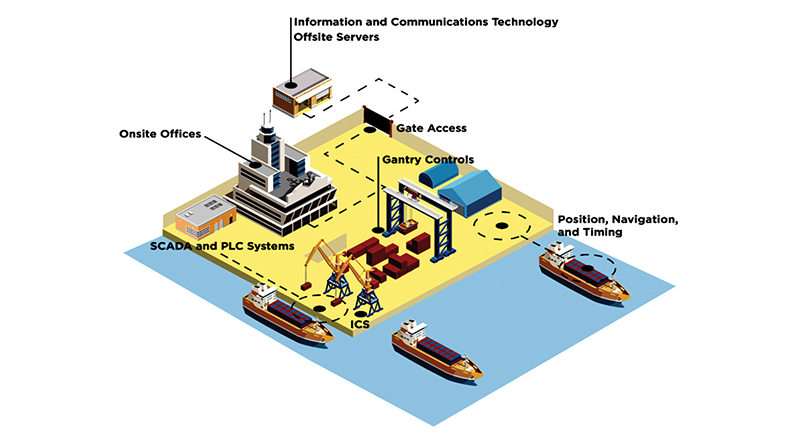
That’s why maritime security is key for supply chain security. Cybersecurity threats can occur at multiple places, including ports, communications systems and ships themselves as shown in Figure 1 (above). The CyberForza Cloud AI Cyber Defense Platform is a part of NEC Corporation of America’s 360-degree approach to port security (refer to NEC’s advertisement on Page 8 for additional information).

Figure 2 — Cyber vulnerability targets and cyberattack surface for the ship
Ports and ships comprise heterogeneous, complex, and often legacy systems. Maritime systems are in a constant state of evolution. Assets are highly interconnected, including both stationary (e.g., land-based) and mobile (e.g., shipboard) infrastructures, and, in many cases, remain in almost constant use. Both fixed and mobile infrastructures are interdependent and interlaced. At their core, they are driven by processes and tools such as data flows, OT (operational technology) systems, OT end devices, ICT (information communication technologies) systems, ICT end devices, cloud infrastructures, networked nodes, communication systems, and safety and security systems. This profusion of systems and components ranges from generic IT and OT devices. Most common cyberattacks on ports and ships are ransomware, phishing, malware, social engineering, brute force, denial of service, ransomware, and other advanced attacks. Out of all these potential cyberattack vectors in terms of vulnerability, volume of exploitation, damage and consequence for the ships are shown on Figure 2.
All ships have complex control systems, communication systems, networks connecting internal systems and outside cloud/satellite network communications. Hackers target easy access to the ship attack surface controls. That leads to significant data breach and taking control of the ship and huge damage done through certain cyberattacks. An example of a cyberattack real live use case follows.
CyberForza analyzed customer real-world cyberattack for ships and ports use case:
CyberForza Eagle Zero Trust Compliant Cloud AI Cyber Defense Platform addresses each step of the hacker lateral movements and provides visibility to ships and ports for cyber resiliency. The Eagle Cyber Defense platform provides external, internal, end point, and other IOT devices level security vulnerabilities on a real time basis.
A cyber hacker can gain access to a port or ship’s systems a number of ways:
Cyber reconnaissance
Targeting a port/ship directly, hackers may first use public and unprotected sources, social media, or manufacturer data to gain information for vulnerabilities. The hacker identifies the weakest link to gain access to data flowing to and from a ship or port. The cyberattack can originate from external, internal or connected devices within the ship or port.
Cyberattack delivery
Cybercriminals attempt to access the company or ship systems and data and deliver malware or steal information. There are several ways in which this can happen via ship online services, websites, network connect, container tracking programs, emails with attached malware or links that can lead to sites with infectious malware.
Cyber breach
When the attacker enters the system and can tamper with data or steal information, it may not always be visible for several days. They can use honey pots or threat bombshells, which are time-bound. The user might not notice for as long as three to six months as some techniques do not hinder the function of programs, but they may be transmitting sensitive data anyway. A data breach can occur and might only become known after the attacker already has full control. Once fully operational, the malware takes over the ship/port control system entirely with software of their own.
Cyber pivot
Once inside your network, cybercriminals will use that access to obtain data which can allow them to get into other systems. They may first choose to attack an area of the company or ship security that is lower and less critical but then can use that information to hack into more sensitive areas. Cybercriminals upload programs and applications that will help them with their next target in the ship/port system. They use tool sets to sense where the mission critical data is residing and install programs that allow them continued access to the ship/port to get data on a regular basis.
Globally, all ports and ships are facing multiple cyberattacks, creating major industry challenges. There is no integrated product that covers port or ship multiple cyberattacks arising from external, internal, end points, and IOT devices. All ports and ships require an advanced AI Cyber Defense Platform for multi-threat detection on a real-time basis to prevent cyberattacks. A critical infrastructure security stack for ports and ships must address operating systems (OS), networks, applications, SCADA Control systems, and IOT devices vulnerabilities. CyberForza provides an integrated cyber defense platform for ports and ships to prevent multiple cyberattacks.
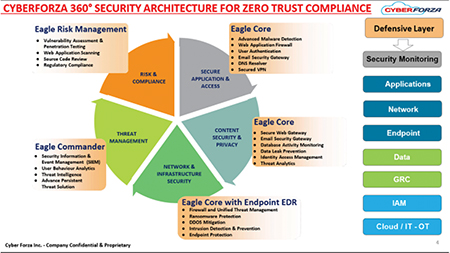
Figure 3 — Zero Trust 3600 Security Architecture for compliance implementation
CyberForza supports ports and ships with a 360-degree Security Architecture for the Zero Trust Compliance implementation as shown in Figure 3. Zero Trust Cyber Architecture covers all users, devices, and policies, whether in or outside the organization’s network, requiring all to be authenticated, authorized, and continuously validated for security configuration and posture before being granted access to applications and data. Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination/hybrid with resources anywhere. Workers in any location can also be identified.
CyberForza provides a complete holistic view of all the “actionable insights” related to the vulnerabilities of ships and ports for security configurations, application, software code changes, command/control system continuous monitoring for a real-time threat hunting with automated governance compliance provided. CyberForza provides coverage for cloud containers, dockers, micro services, and dev ops security. CyberForza’s comprehensive coverage includes application security testing, vulnerability management, compliance automation, and threat detection and response.
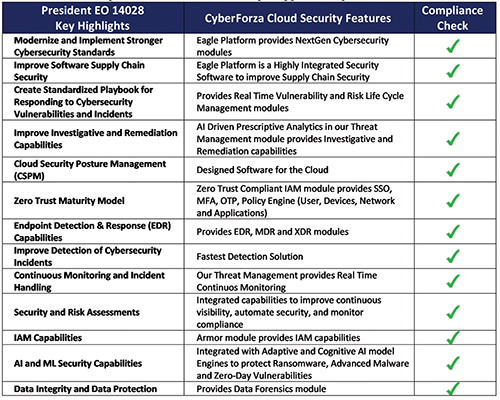
The CyberForza Eagle Commander threat hunting module covers all aspects of mission critical cybersecurity hygiene building process for the ports and ships. CyberForza Eagle Cyber Defense Platform complies with NIST 800-53/FedRAMP, NIST-800-52, NIST 800-171, NIST CSF, ISO-27001, PCI-DSS, HIPPA, SOC-2 & 3, SOX, GDPR, and ITG Standards. Presidential Executive Order compliance for ports and ships supported is shown in the table shown below.
The Eagle Integrated Cloud AI Cyber Defense Platform Architecture unique differentiation is illustrated in Figure 5 (below). Eagle Integrated Cyber Defense Platform modules are interoperable with a port or ship’s existing cyber legacy infrastructure. CyberForza provides a complete security gap analysis to be able to identify vulnerabilities, risk mitigation, cybersecurity hygiene plan, cyber operating procedures, and cyber awareness for staff development.
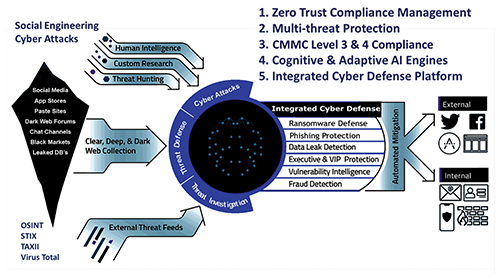
Figure 4 — CyberForza Zero Trust Compliance Architecture unique differentiators
The Eagle Cyber Defense Platform defends from external threats, internal threats, end point threats, SCADA, ICT threats and complete vulnerabilities and risk management for ships and ports as noted in Figure 4.
Eagle Cloud AI Cyber Defense Platform value proposition
- As part of the NEC suite of security products, Zero Trust Compliance Cyber Defense provides for multi-threat protection for ships and ports.
- Single sign-on, multi-factor authentication, one-time password, dynamic identity access management controls. CyberForza/NEC brings together facial recognition for the smart sea workspace.
- Integrated threat management (SIEM, SOC & SOAR Integrated) provides real-time managed detection response (MDR) with an end-point detection response (EDR) system
- Gain real-time visibility and secure your business-critical applications through CyberForza Zero Trust Integrated Cyber Defense Platform
- Unified vulnerability management and risk management for ships and ports
- Customer benefits of using Eagle Cyber Defense Platform:
Tight integration with NEC’s physical port security protection suite (see article in the September 2021 issue of Pacific Ports Magazine, Page 40)
- No capital equipment purchase expense (CAPEX)
- Security software as service (SaaS) business model
- Operational expenses (OPEX) reduced by 20 percent
- Security operational efficiency increased by 35 percent
- Interoperates with legacy platforms in parallel to protect a customer’s cyber investment, including easy upgrades for Cloud migration
- Return on investment is less than two months (one data breach can cost an average of over $5 million)
- By Dr. Venkat Rayapati, Founder, Chairman, & CEO, CyberForza Inc. — Dr. Rayapati holds a Doctoral degree in Electrical and Computer Engineering from University of Montreal, Canada and has published about 35 papers in various reputable International Journals and Conferences.
For more information, visit: www.necam.com/IntelligentSecurity